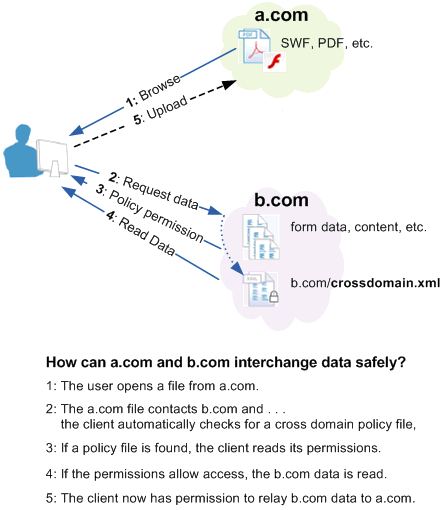
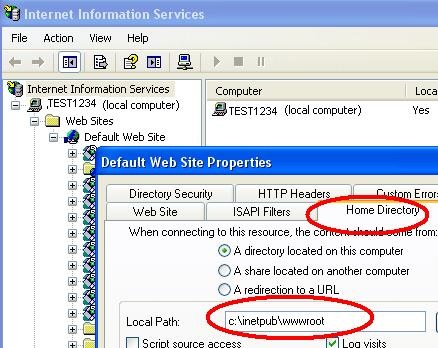
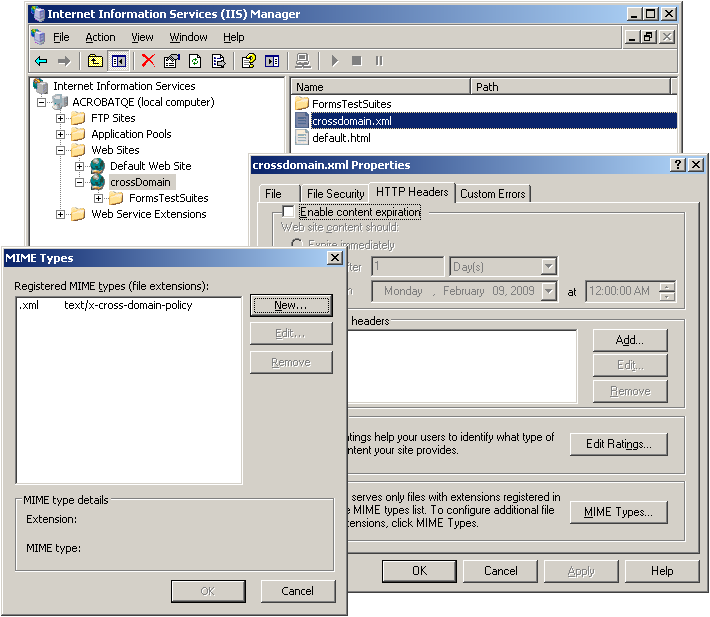
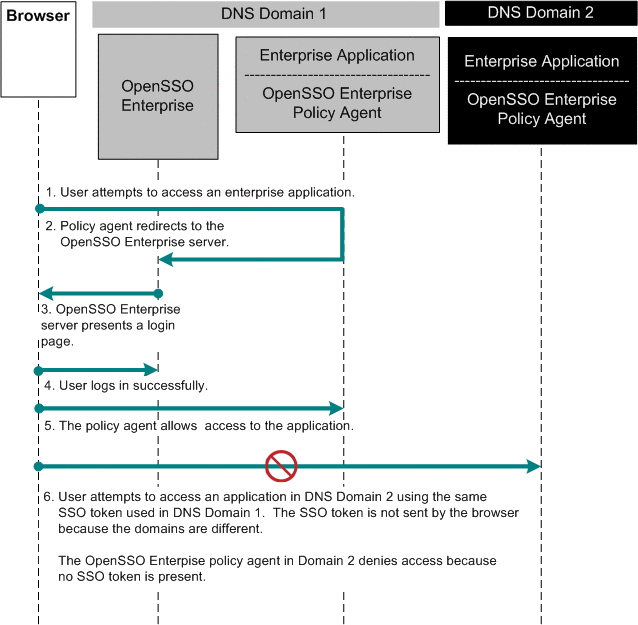
group policy - Creators Update Stops Cross Domain GPO Drive mapping working ('0x80090005 Bad Data) - Server Fault
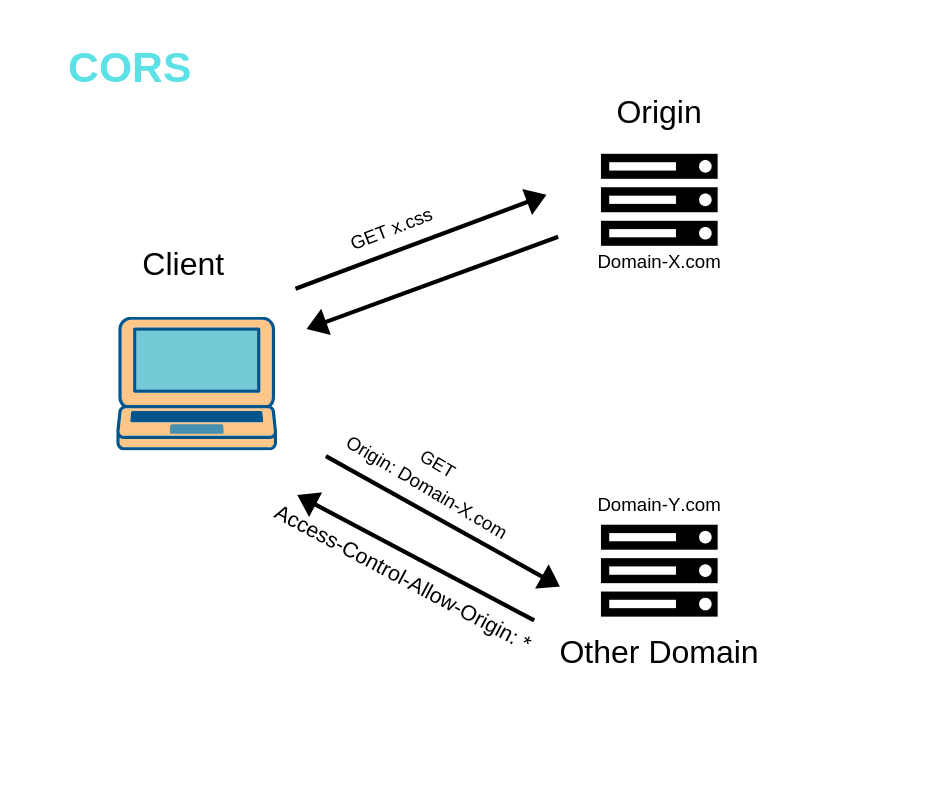
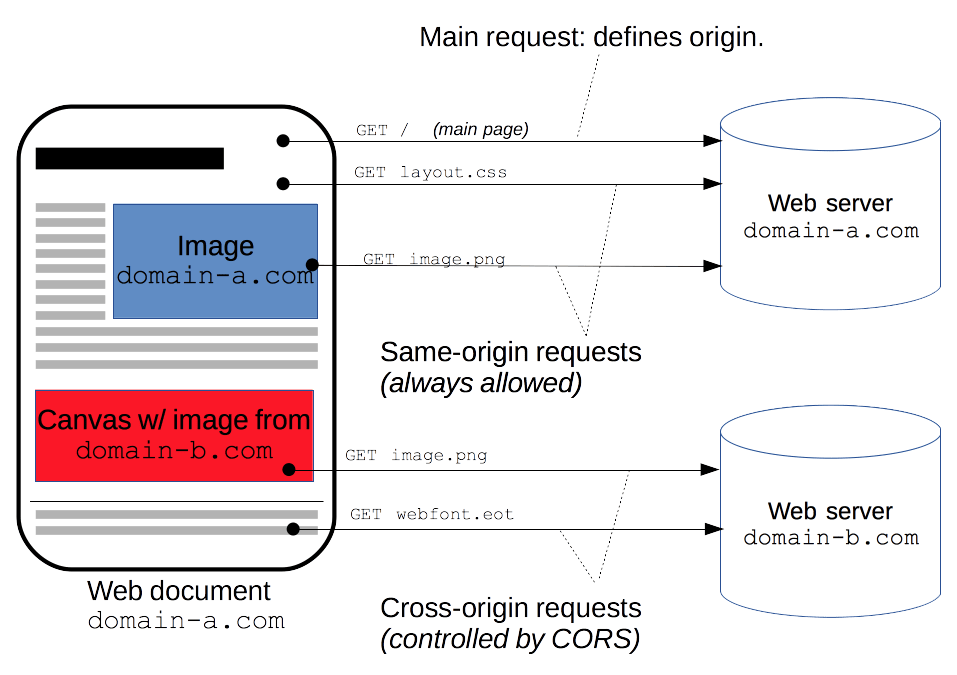
6 Must-Know Things About Cross-Origin Resource Sharing (CORS) | by GP Lee | JavaScript in Plain English

Random Security: Exploiting Insecure crossdomain.xml to Bypass Same Origin Policy (ActionScript PoC)
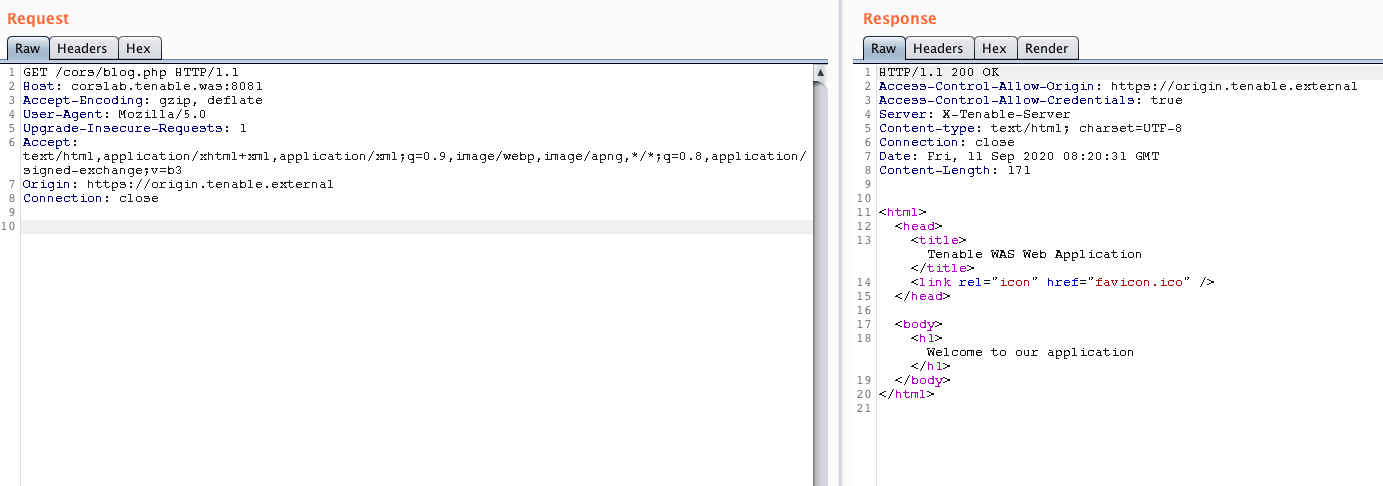
![PDF] An empirical study on the security of cross-domain policies in rich internet applications | Semantic Scholar PDF] An empirical study on the security of cross-domain policies in rich internet applications | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/8b988165c663836cc5de52df21fa7c3b528e269d/5-Figure6-1.png)
![Cross domain policy [8]. | Download Scientific Diagram Cross domain policy [8]. | Download Scientific Diagram](https://www.researchgate.net/publication/320108029/figure/fig13/AS:544025849626632@1506717278659/Cross-domain-policy-8.png)

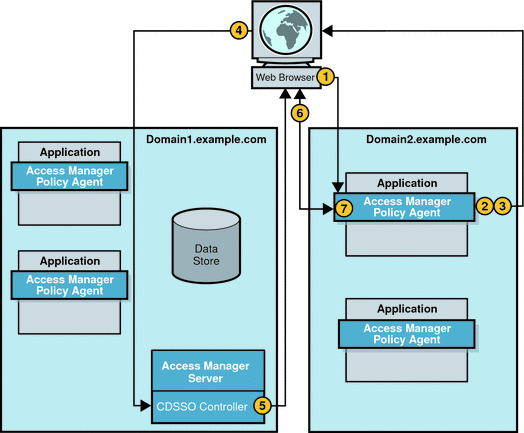
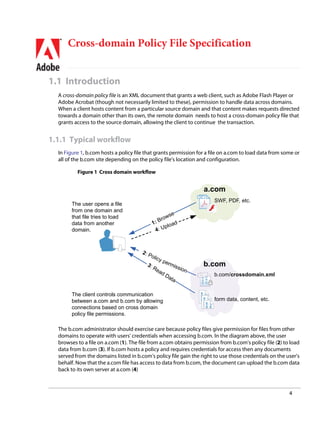
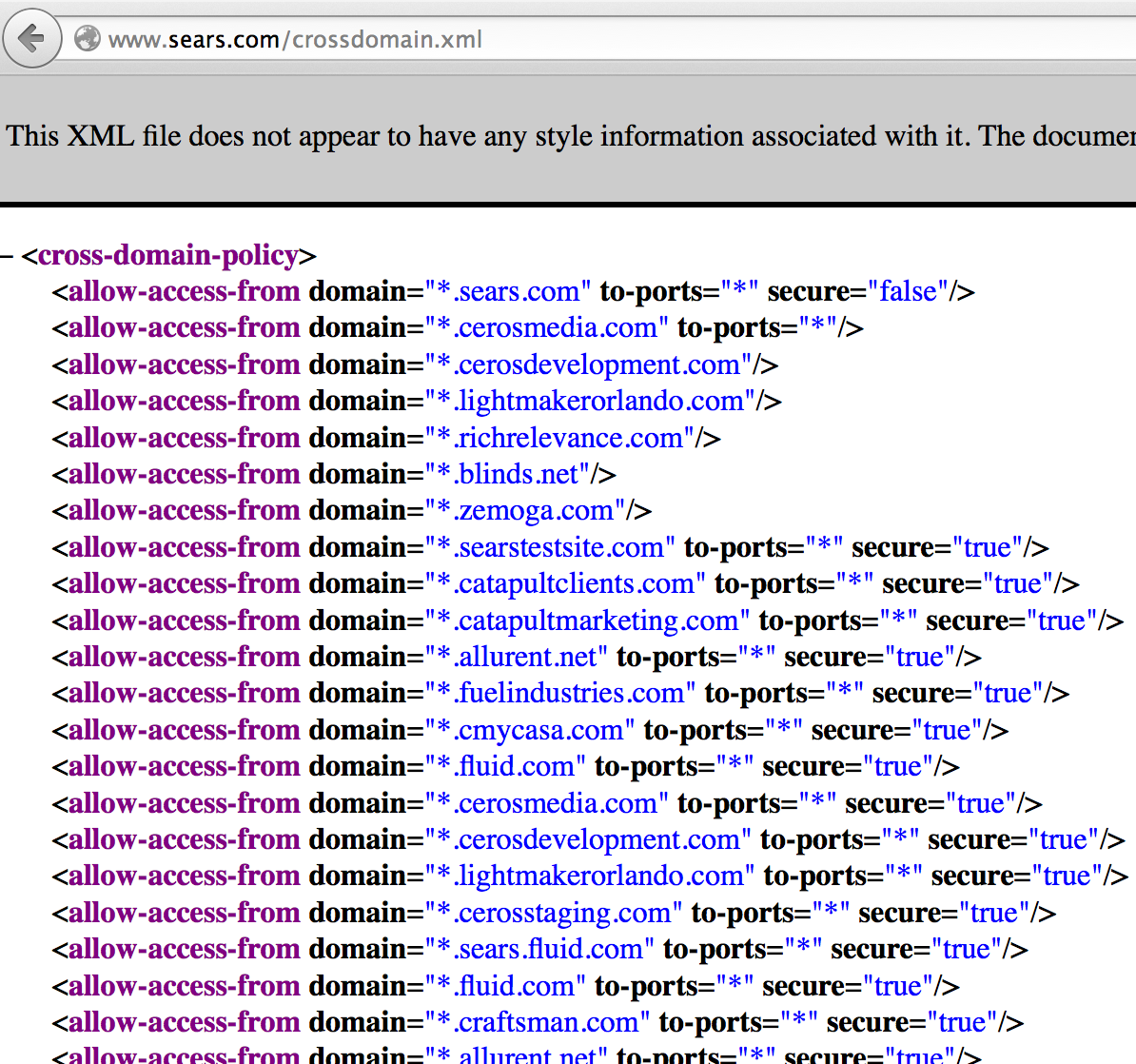

![PDF] Analyzing the Crossdomain Policies of Flash Applications | Semantic Scholar PDF] Analyzing the Crossdomain Policies of Flash Applications | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/2d3f01f83330c1878411004fb5dc979ddd7440d2/4-Figure3-1.png)